Learning Library
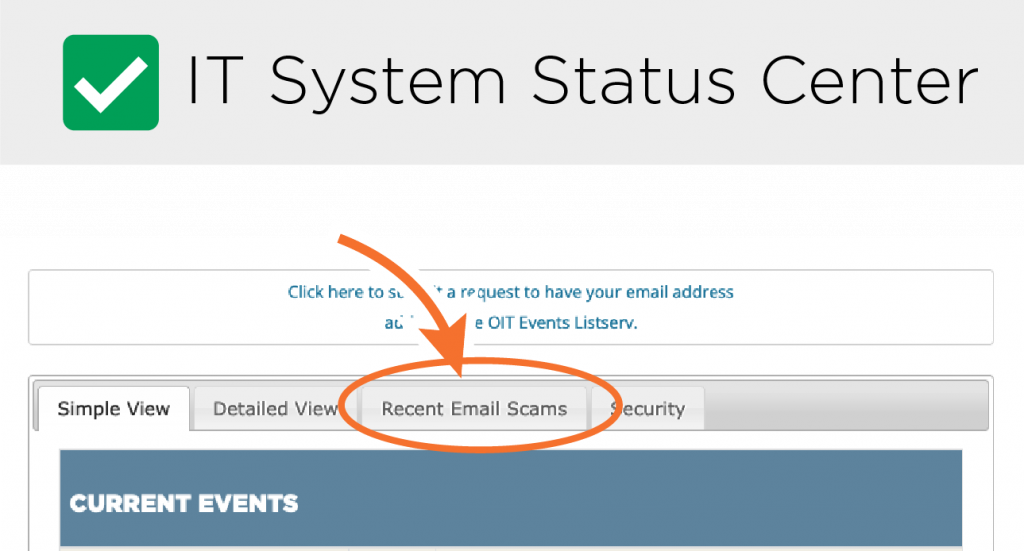
Check for Recent Email Scams
Email scams are an ever-evolving threat in this digital world. It can be hard to tell what is real and what is the latest bit of social engineering. Cross check suspicious emails at the Status Center! We log recently reported scams in the UT email ecosystem that you can compare your email to. Stay informed!
Importance of Security
Read about why YOU should care about security and what we are doing to keep your data safe.
Protecting University Data
Learn how to protect university data by managing systems and applications responsibly.
Terms & Glossary
There is a lot of jargon when discussing security. Here is a glossary to help break it down.
Recent Articles
The Essential Role of Security Awareness Training in Safeguarding Our Campus Community
Published on July 15, 2024
In the ever-evolving digital landscape of higher education, the importance of security awareness cannot be overstated. Whether you’re a student […]
ReadThe Essential Role of Security Awareness Training in Safeguarding Our Campus CommunitySecure Data Management: A Keystone of Cybersecurity
Published on July 3, 2024
In today’s interconnected world, managing data securely is not just a responsibility of the IT department; it’s a mission for […]
ReadSecure Data Management: A Keystone of CybersecurityThe Essential Guide to Incident Response Planning
Published on June 28, 2024
In the digital age, where cyber threats are as common as they are diverse, one of the most critical aspects […]
ReadThe Essential Guide to Incident Response PlanningStay Safe and Connected: The Importance of Reporting Incidents to OIT
Published on June 23, 2024
In today’s ultra-connected world, where technology is interwoven into every aspect of our lives, it’s essential to stay vigilant about […]
ReadStay Safe and Connected: The Importance of Reporting Incidents to OIT
 Explore
Explore Write
Write Chat
Chat Call
Call